F.A.Q.
Q: Where can I sign-up for an account?
A: Fill out the registation form.
Q: I forgot my password. How do I reset it?
A: Please have a colleague reset your password in the application or email Solutions@BlackCatWhiteHatSecurity.com for help.
Q: Do you have a lock out period for unsuccessful sign-ins?
A: Yes, you have a couple and a few attempts to sign-in successfully. If you get locked out, email Solutions@BlackCatWhiteHatSecurity.com for help.
Q: Why can't I use self-service password resets?
A: Manual and automated self-service password resets can put systems at risk, since they are highly vulnerable to social engineering attacks.
Q: Do you store any information from API configurations?
A: We use your API key to connect to these services. Your API information is encrypted within our system. No data is stored unless you use our import functionality to create risk profiles, assets or Microsoft Secure Score.
Q: How secure will my data be with Black Cat White Hat Security L.L.C.?
A: We compare our product to OWASP Top 10 Web Application Security Risks and use many technologies to secure your data. We protect from SQL Injections, HTML Injections and more!
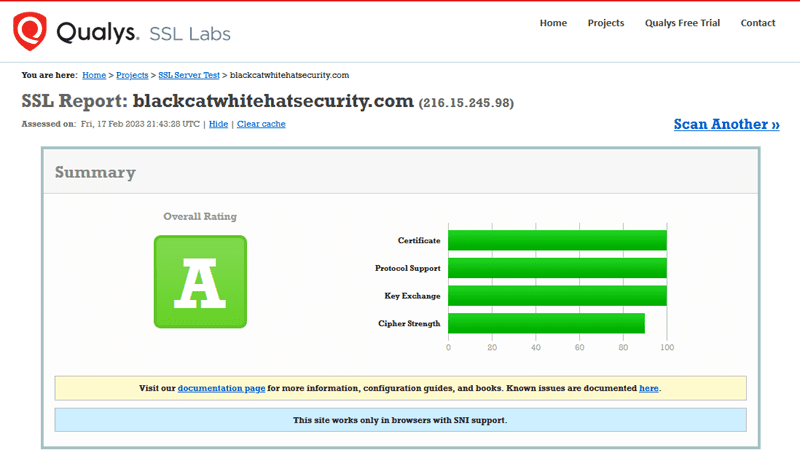
Q: How secure is your SSL certificate?
A: We currently use Let's Encrypt and other server technologies for a secure connection. Here are the results from Qualys SSL Labs Report.
Q: What should I expect as an end user when you implement the steps involved with Microsoft's Secure Score?
A:
The implementation of Microsoft's secure score will likely result in improved security for your organization's digital assets and data. Here are a few things you might expect:
1) Increased awareness of potential security risks: The first step in implementing Microsoft's secure score involves identifying potential security risks and vulnerabilities within your organization's digital environment. As an end user, you may be asked to participate in security awareness training and/or to be more vigilant about protecting your own devices and data.
2) Changes to your organization's security policies and practices: Based on the results of the secure score analysis, your organization may need to make changes to its security policies and practices. For example, you may be required to use stronger passwords, to update your devices more regularly, or to follow new procedures for accessing sensitive data.
3) Enhanced security features in Microsoft products: Microsoft's secure score is designed to help organizations get the most out of the security features included in Microsoft products. As an end user, you may notice changes to the user interface of certain apps or programs, or you may be prompted to use new security features, such as multi-factor authentication or data encryption.
4) Improved communication and collaboration with IT staff: As your organization works to implement Microsoft's secure score, you may find that you have more opportunities to communicate and collaborate with IT staff. For example, you may be asked to report any security incidents or suspicious activity you encounter, or to provide feedback on new security features or policies.
Microsoft's Secure Score is to improve the security of your organization's digital environment, and as an end user, you can expect to play an important role in this process. By working with your IT staff and following new security policies and procedures, you can help protect your organization's data and assets from potential threats.
Q: What is HIPPA and PII?
A: HIPAA (Health Insurance Portability and Accountability Act) is a federal law in the United States that provides privacy and security protections for certain health information. It sets standards for the protection of individuals' medical records and other personal health information. HIPAA applies to covered entities, which include health care providers, health care clearinghouses, and health plans.
PII (Personally Identifiable Information) is any information that can be used to identify a specific individual. Examples of PII include names, addresses, Social Security numbers, driver's license numbers, and email addresses. PII can be sensitive and is often subject to privacy laws and regulations, including HIPAA. Protecting PII is important to prevent identity theft, fraud, and other forms of misuse.
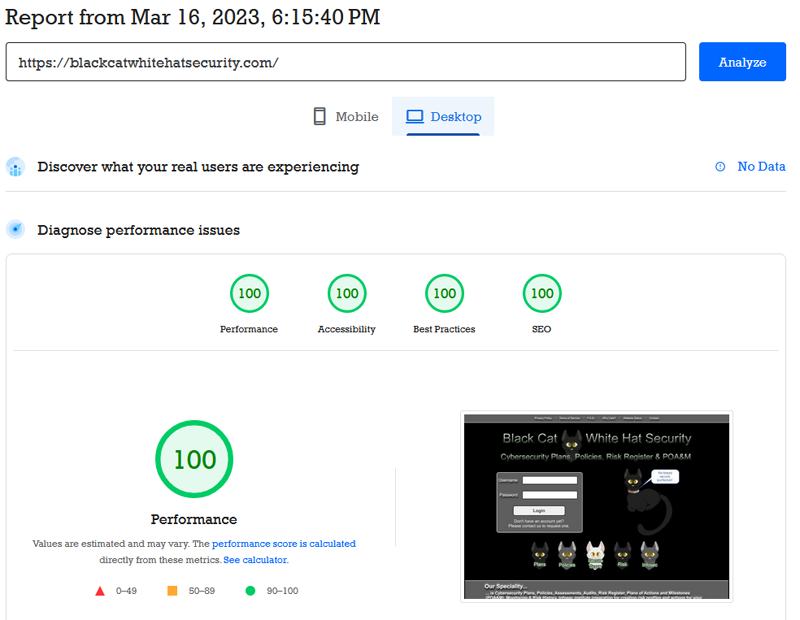
Q: What are the results with PageSpeed Insights?
A: 100%
|
![]() Donate
Donate
![]() Endpoint
Endpoint
![]() F.A.Q.
F.A.Q.
![]() Privacy
Privacy
![]() Sales
Sales
![]() Status
Status
![]() T.O.S.
T.O.S.
![]() Contact
Contact
![]()
![]()
![]()
![]()
![]()


